0 Crypter
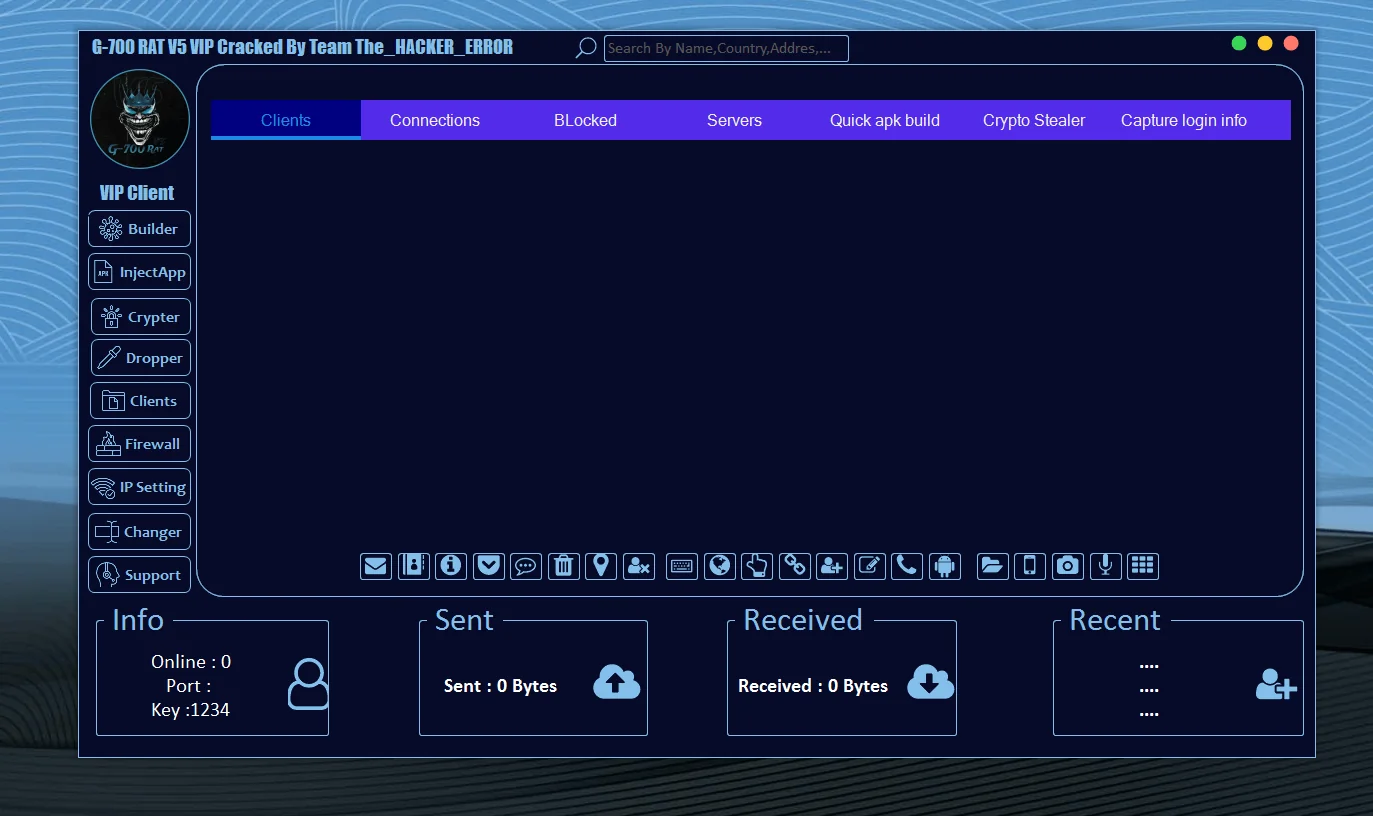
0 Crypter 2023 In the world of cybersecurity, there are many tools and techniques used by both ethical hackers and malicious actors. One such tool that has gained attention in recent years is the 0 Crypter, a piece of software designed for the specific purpose of encrypting malware, making it harder for traditional antivirus programs to detect. While its name may not be as well-known as some major viruses or malware families, the 0 Crypter plays a crucial role in the operation of modern cyberattacks, particularly in the field of ransomware and other types of malicious software.
This essay explores the functionality of the 0 Crypter, its role in cybercrime, the mechanisms behind its encryption techniques, and the challenges it poses to cybersecurity professionals. Additionally, it will highlight the implications of such tools for digital safety and the evolving nature of cybersecurity threats.
What is 0 Crypter?
At its core, 0 Crypter is a software tool used by cybercriminals to obfuscate or encrypt malicious code, effectively making it invisible to antivirus programs. The term “crypter” comes from the word “encrypt,” referring to the practice of encoding a piece of data (in this case, a virus or malware) to make it difficult to understand or detect without the proper decryption key or method. The purpose of encryption is to modify the malware’s code so that traditional security software, which relies on pattern recognition or signature-based detection, cannot identify the threat.
Crypters like 0 Crypter are often used by attackers to deploy undetected payloads on victims’ machines, often facilitating ransomware attacks, data theft, or other forms of cyber intrusion. This obfuscation makes the malware harder to reverse-engineer, significantly prolonging the time it takes for antivirus vendors to develop signatures for detection.
How 0 Crypter Works
To understand how 0 Crypter works, it’s necessary to first understand the basic process of malware encryption. When a cybercriminal wants to infect a victim’s system, they may craft a piece of malware that carries out a specific attack, such as file encryption (ransomware) or a remote access tool (RAT). However, many antivirus programs have databases of known malware signatures, which allow them to identify and block previously discovered threats.
Here’s where the 0 Crypter comes into play. It encrypts the malicious payload before the attacker delivers it to the target system. The encryption process alters the malicious code’s appearance, often by using a random encryption key that will be stored within the software. The encrypted payload is then delivered, and once it reaches the victim’s system, the crypter decrypts it, allowing the malware to execute its intended action without being detected.
There are various techniques employed by crypters, including polymorphism and metamorphism. In polymorphism, the crypter generates different versions of the same malware with each infection, changing the encryption key or the way the code appears. Metamorphism takes this further, completely changing the structure of the code while preserving its original functionality. This helps evade both signature-based and behavior-based detection methods.
Additionally, crypters may use packers, which compress or wrap the malicious code in layers, making it appear benign at first glance. When the code is executed, it decompresses and activates the actual malicious payload.
Role of 0 Crypter in Cybercrime
0 Crypter, like other encryption tools, is commonly used in various types of cybercrime activities. The most significant of these is ransomware, a form of malware where the attacker encrypts the victim’s files and demands a ransom for the decryption key. The ability to encrypt the ransomware payload and prevent detection by antivirus software significantly increases the chances of a successful attack.
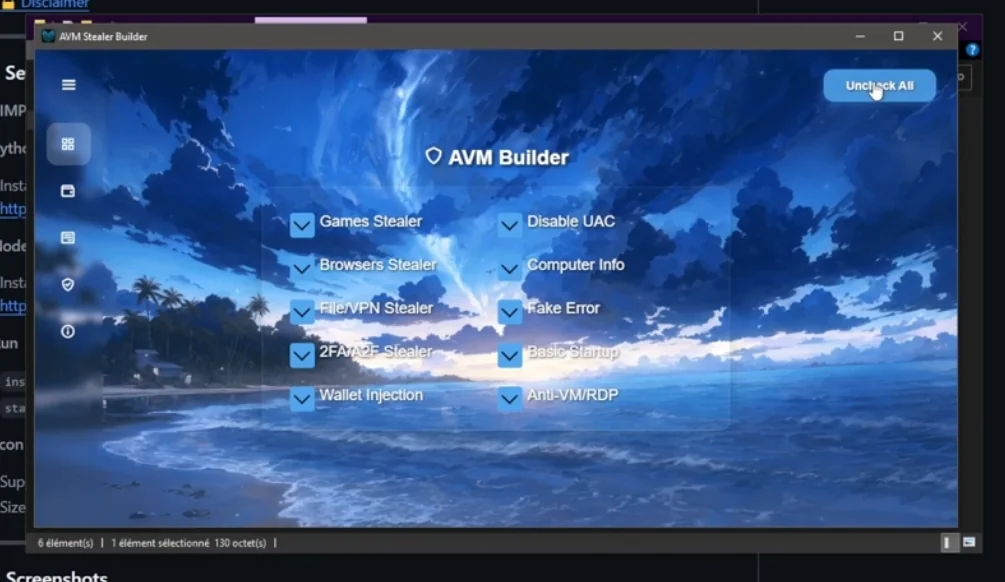
Another common use of 0 Crypter is in spyware and information theft. Cybercriminals use crypters to deploy tools that capture sensitive data, such as usernames, passwords, and credit card information, from unsuspecting victims. By encrypting these tools, the attacker can maintain stealth, avoiding detection while continuously siphoning off valuable information.
In some cases, 0 Crypter can be used to deliver botnet agents, which turn compromised machines into remote-controlled “zombies” in a network used for further attacks, such as Distributed Denial of Service (DDoS) attacks or spam campaigns.
Challenges in Defeating Crypter-Based Malware
The presence of crypters like 0 Crypter represents a significant challenge for traditional antivirus software and other cybersecurity measures. Signature-based detection methods, which rely on recognizing known malware patterns, are ineffective against encrypted payloads because the encryption alters the malware’s signature.
To counteract these threats, cybersecurity professionals have turned to behavior-based analysis, where the system monitors the behavior of files and processes rather than relying solely on signatures. This approach looks for suspicious actions such as unusual system modifications, file encryption, or data exfiltration, even if the malware itself is encrypted.
Another technique used to combat crypter-based malware is heuristic analysis, which involves analyzing code for characteristics or patterns that may indicate malicious intent, even if the exact code is unknown. While these methods are more effective than signature-based detection, they still require constant updates and improvements to stay ahead of new, evolving threats.
The development of sandboxing technology has also proven valuable. In this approach, files are executed in a controlled, isolated environment (the “sandbox”), where their behavior can be observed without risking damage to the actual system. This allows security software to detect malicious actions, such as file encryption or system changes, even if the underlying malware is still hidden.
Implications for Cybersecurity
The existence of tools like 0 Crypter underscores the need for constant vigilance in the realm of cybersecurity. As cybercriminals develop more sophisticated methods to evade detection, cybersecurity solutions must evolve in tandem.
It’s important to note that crypters like 0 Crypter are not inherently illegal; they can also be used for legitimate purposes, such as protecting intellectual property or conducting penetration testing. However, their widespread use in criminal activities highlights the ongoing cat-and-mouse game between attackers and defenders in the digital space.
Organizations and individuals must take a proactive approach to cybersecurity, utilizing a combination of up-to-date antivirus software, behavioral monitoring, network defense measures, and user awareness training. As the threat landscape continues to evolve, so too must the strategies to combat it.
Conclusion
The rise of encryption tools like 0 Crypter has made the landscape of cybercrime more challenging and dangerous. These tools play a critical role in making malware harder to detect, forcing cybersecurity professionals to adapt to new and evolving threats. As cybercriminals continue to refine their techniques, cybersecurity measures will need to keep pace with the growing complexity of attacks.
Understanding the inner workings of tools like 0 Crypter is essential in the fight against digital threats. By staying informed and continuously updating security practices, individuals and organizations can better protect themselves from the dangers posed by this evolving form of cyberattack.