SlayerRAT v0.7.2 By X-Slayer
<
h1><img class=”aligncenter size-medium” ” src=”https://i.postimg.cc/RFs9y3G9/Screenshot-1.png” alt=”slayer” width=”955″ height=”499″ style=”display:none”>
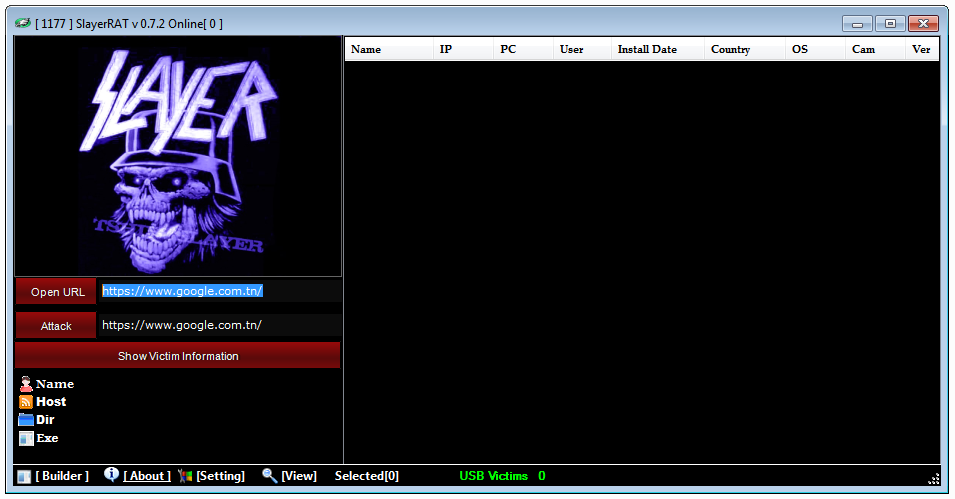
SlayerRAT v0.7.2 By X-Slayer
Slayer RAT is a Remote Access Trojan that has been in use since at least 2013. RATs like Slayer are malicious programs that allow an attacker to take control of a victim’s computer and access sensitive information without the victim’s knowledge. RATs can be used for a variety of purposes, including stealing personal data, conducting espionage, or launching cyberattacks.
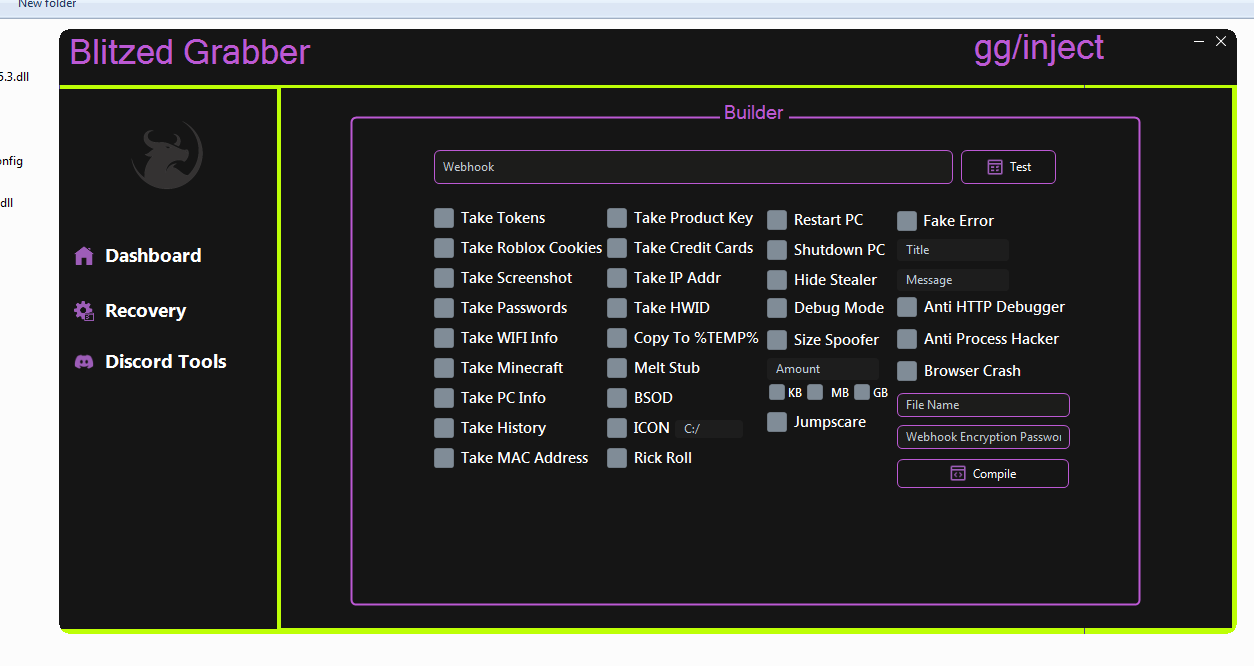
Slayer RAT is known for its sophisticated features and functionality. It is designed to be stealthy, making it difficult to detect and remove. It is capable of capturing keystrokes, taking screenshots, and recording audio and video. It can also steal passwords, login credentials, and other sensitive information. Slayer RAT can be used to remotely control a victim’s computer, giving the attacker full access to the system.
One of the key features of Slayer RAT is its ability to bypass antivirus and other security software. It uses advanced techniques to evade detection and remain hidden on the victim’s computer. For example, it can encrypt its code to avoid detection by signature-based antivirus programs. It can also inject its code into legitimate system processes to avoid detection by behavior-based security software.
Slayer RAT is typically distributed through phishing emails, malicious websites, or social engineering tactics. Once a victim downloads and executes the malware, the attacker gains remote access to the victim’s computer. The attacker can then use Slayer RAT to steal data, plant additional malware, or launch other attacks.
To protect against Slayer RAT and other Remote Access Trojans, it is important to practice good cybersecurity hygiene. This includes using strong and unique passwords, keeping software and security patches up to date, and being cautious when opening email attachments or clicking on links. It is also important to use antivirus and other security software to detect and remove malware.
In conclusion, Slayer RAT is a sophisticated and dangerous Remote Access Trojan that can be used for a variety of malicious purposes. It is designed to be stealthy and difficult to detect, making it a significant threat to cybersecurity. To protect against RATs like Slayer, individuals and organizations should take steps to improve their cybersecurity practices and use security software to detect and remove malware.
yahoo:kbksrb@ymail.com
ICQ:653580170
jabber: bilalkhanicompk@jabber.ru