RPS420 RAT: The Stealthy Windows Remote Access Trojan Explained
In the shadowy world of cybersecurity threats, few malware tools strike as much fear as Remote Access Trojans (RATs). Among them, the RPS420 RAT stands out as a particularly insidious piece of software, designed for stealthy infiltration and total system domination. If you’ve landed here searching for “RPS420 RAT,” you’re likely concerned about its capabilities, how it sneaks onto your Windows machine, or—most importantly—how to fight back. This comprehensive guide dives deep into what the RPS420 RAT is, its advanced features, detection methods, and removal strategies. Whether you’re a cybersecurity enthusiast or a worried user, arm yourself with knowledge to stay one step ahead of these digital intruders.
As cyber threats evolve, understanding tools like the RPS420 RAT isn’t just informative—it’s essential. Sold in underground markets and touted as a “powerful Windows RAT stealer miner tool,” this malware combines data theft, surveillance, and resource hijacking into one nightmare package. Let’s break it down.
What Is RPS420 RAT?
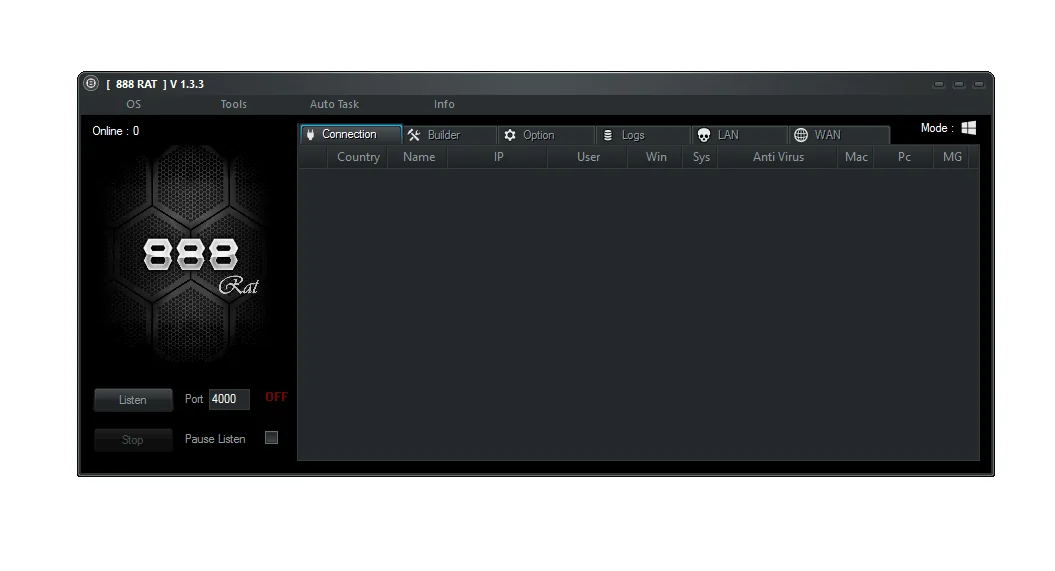
The RPS420 RAT is a sophisticated Remote Access Trojan targeting Windows operating systems, from Windows 7 all the way up to Windows 11. Unlike benign remote desktop tools, RATs like RPS420 are built for malicious intent: granting unauthorized attackers full control over infected devices. It’s often marketed in hacking forums and dark web stores as a multi-feature tool for espionage, financial theft, and persistent surveillance.
At its core, RPS420 RAT functions as a backdoor, allowing remote command execution while remaining hidden from casual users. It was first spotted in underground repositories around mid-2025, with builders and source code circulating on platforms like GitHub and Telegram channels dedicated to malware distribution. Developers emphasize its “stealthy” nature, using obfuscation techniques to dodge antivirus scans and evade sandboxes.
What sets RPS420 apart from older RATs like DarkComet or njRAT? Its integration of stealer (data theft), miner (cryptocurrency hijacking), and RAT functionalities in one payload. This all-in-one approach makes it a favorite among cybercriminals targeting individuals, small businesses, and even larger organizations. According to security mirrors, the tool’s archive weighs in at around 40MB, packed with executables and configuration files for customization.
In short, if RPS420 RAT infects your system, it’s not just spying—it’s potentially draining your wallet and turning your PC into a zombie in a botnet.
Key Features of RPS420 RAT
The RPS420 RAT isn’t your average trojan; it’s loaded with features that make it a Swiss Army knife for hackers. Here’s a breakdown of its standout capabilities, drawn from leaked documentation and product descriptions:
1. Comprehensive File and System Management
- Browse, upload, download, delete, or rename files and directories remotely.
- Create or delete folders, giving attackers easy access to sensitive data like documents or backups.
- Enumerate installed software, hardware specs, and even printers for reconnaissance.
2. Surveillance and Monitoring Tools
- Keylogging: Captures every keystroke, snagging passwords, emails, and chat messages in real-time.
- Screen and Webcam Capture: Takes screenshots or records video feeds from your camera without any visual cues.
- Audio Recording: Listens in via your microphone, turning your device into a bugging device.
- Clipboard Theft: Steals copied text, like credit card details or crypto keys.
3. Data Exfiltration and Theft
- Password Stealer: Pulls credentials from major browsers (Chrome, Firefox, Edge) and apps.
- Cryptocurrency Wallet Hijacking: Scans for and exfiltrates wallet files from Bitcoin, Ethereum, and other coins—perfect for its built-in miner module.
- Browser Data Grab: Extracts history, bookmarks, cookies, and autofill info for identity theft.
4. Remote Control and Persistence
- Execute CMD or PowerShell commands remotely.
- Full remote desktop streaming for live control.
- Persistence Tricks: Adds itself to startup, creates scheduled tasks, or uses USB autorun to spread to other machines.
- Turns infected PCs into FTP servers for easy file transfers.
5. Evasion and Anti-Analysis
- Detects virtual machines, debuggers, and sandboxes to self-destruct or hide.
- Disables security features like Task Manager, Registry Editor, Command Prompt, and antivirus tools.
- Uses encrypted C2 (command-and-control) communication with dynamic ports to slip past firewalls.
These features make RPS420 RAT incredibly versatile, supporting everything from local LAN attacks to out-of-network remote exploitation. But with great power comes great risk—let’s explore how it operates.
How Does RPS420 RAT Work?
Deploying and operating RPS420 RAT follows a classic malware lifecycle, but with modern twists for evasion.
Infection Vectors
Attackers typically deliver RPS420 via phishing emails, malicious downloads, or drive-by exploits on compromised sites. Once executed, the payload (often a disguised .exe) installs silently. It can spread through USB drives using autorun.inf tricks or exploit LAN vulnerabilities for lateral movement.
Command-and-Control Setup
The RAT phones home to a hacker-controlled C2 server using encrypted channels—think HTTPS or custom protocols—to avoid network filters. A web-based GUI lets the attacker manage multiple bots, issuing commands like “capture screenshot” or “steal passwords.”
Persistence and Evasion in Action
To stick around, RPS420 injects itself into legitimate processes (process hollowing) and uses obfuscated code that changes signatures on the fly. If it detects analysis tools, it might fake crashes or delete traces. Data like keystroke logs or stolen creds gets bundled and exfiltrated periodically, often compressed to minimize traffic.
In tutorials circulating online, setup involves VMware for testing, port forwarding for firewall bypass, and custom builders for payload tailoring. The result? A ghost in your machine that could linger for months undetected.
The Risks and Impacts of RPS420 RAT Infection
An RPS420 RAT breach isn’t just inconvenient—it’s devastating. Financial losses from stolen crypto or credentials can run into thousands. Privacy erosion through webcam spying leads to blackmail (sextortion scams are rampant). For businesses, it means IP theft, ransomware pivots, or botnet recruitment for DDoS attacks.
Worse, its miner component silently uses your GPU/CPU to mine Monero or other coins, spiking electricity bills and hardware wear. In 2025 alone, RAT-driven cryptojacking incidents surged 40%, per cybersecurity reports, with tools like RPS420 fueling the trend.
How to Detect RPS420 RAT on Your System
Spotting RPS420 RAT early is tough due to its stealth, but vigilance pays off. Here’s a step-by-step detection guide:
1. Monitor System Behavior
- Unusual CPU/GPU usage? Check Task Manager for rogue processes (e.g., svchost.exe spikes).
- Slow performance, random reboots, or webcam lights activating solo? Red flags.
2. Use Antivirus and EDR Tools
- Run full scans with updated software like Malwarebytes, ESET, or Windows Defender. RPS420’s obfuscation might slip by, but behavioral detection catches anomalies.
- Advanced Endpoint Detection and Response (EDR) like CrowdStrike flags C2 traffic.
3. Check Network Activity
- Tools like Wireshark reveal outbound connections to unknown IPs. Look for encrypted traffic on non-standard ports.
- Review firewall logs for port forwarding attempts.
4. Inspect Startup and Processes
- Use Autoruns (from Sysinternals) to scan for suspicious entries in startup folders or scheduled tasks.
- Process Explorer can reveal hidden PIDs tied to RAT activity.
5. Behavioral Analysis
- If you suspect infection, boot into Safe Mode and scan. Tools like Process Hacker help identify faked processes.
For RPS420 specifically, watch for its hallmarks: browser credential dumps or USB autorun files. Remember, no single method is foolproof—layer your defenses.
Step-by-Step Guide to Removing RPS420 RAT
Once detected, swift removal is key. Follow these steps carefully:
1. Isolate the Device
- Disconnect from the internet immediately to halt C2 communication.
- Avoid using the machine for sensitive tasks.
2. Boot into Safe Mode
- Restart and enter Safe Mode (hold Shift during reboot) to limit RAT activity.
3. Run Malware Removal Tools
- Use AdwCleaner or HitmanPro for initial cleanup.
- Follow with a deep scan from your AV—quarantine anything flagged.
4. Manually Purge Traces
- Delete suspicious files from %AppData%, Temp folders, and startup entries.
- Reset browsers to defaults and change all passwords from a clean device.
- Uninstall unknown programs via Control Panel.
5. Advanced Cleanup
- Use Autoruns to disable persistence mechanisms.
- If needed, wipe and reinstall Windows—extreme but effective for stubborn infections.
6. Post-Removal Checks
- Monitor for reinfection and update all software.
- Enable multi-factor authentication (MFA) everywhere.
Pro tip: For RATs like RPS420, professional help from IT security firms can uncover hidden payloads.
Prevention: Staying Safe from RPS420 RAT and Similar Threats
Prevention beats cure. Here’s how to fortify your defenses:
- Patch Everything: Keep Windows and apps updated to close exploit doors.
- Antivirus with Real-Time Protection: Opt for solutions with RAT-specific heuristics.
- Email and Download Caution: Verify attachments and avoid shady sites. Use sandboxing for unknowns.
- Network Security: Firewalls, VPNs, and zero-trust models block lateral spread.
- User Education: Train on phishing recognition—most infections start with a click.
- Regular Backups: Offline storage ensures quick recovery without paying ransoms.
By implementing these, you slash your RAT risk dramatically.
Frequently Asked Questions (FAQ) About RPS420 RAT
What is RPS420 RAT?
RPS420 RAT is a malicious Remote Access Trojan designed for Windows systems. It combines remote control, data theft (stealer), and cryptocurrency mining capabilities into a single stealthy payload, often sold in underground hacking forums.
How does RPS420 RAT infect a computer?
It typically spreads via phishing emails, malicious downloads, cracked software, or USB drives with autorun. Once executed, it installs silently and establishes a connection to a hacker’s command-and-control (C2) server.
Can antivirus detect RPS420 RAT?
Some antivirus programs can detect known variants, but its heavy obfuscation and anti-analysis features often allow it to evade signature-based detection. Use behavioral analysis tools and keep definitions updated.
Is RPS420 RAT still active in 2025?
Yes. As of October 2025, new builds and source code leaks continue to appear on GitHub mirrors, Telegram channels, and dark web marketplaces, indicating active development and distribution.
Does RPS420 RAT work on Windows 11?
Yes. It supports all modern Windows versions, including Windows 11, and uses compatibility tricks to bypass User Account Control (UAC) and SmartScreen warnings.
Can RPS420 RAT steal cryptocurrency?
Absolutely. It includes a built-in wallet stealer that targets Bitcoin, Ethereum, Monero, and other popular crypto wallets, alongside a cryptominer that hijacks your GPU/CPU.
How do I know if my webcam is being spied on by RPS420 RAT?
Look for unexpected webcam activity (light turns on), unexplained video files in Temp folders, or high network upload traffic. Use tools like Who’s Using My Webcam? to monitor access.
Is it safe to remove RPS420 RAT manually?
Manual removal is possible but risky. Always isolate the device, use Safe Mode, and back up data first. For full confidence, consider professional malware removal or a clean OS reinstall.
Can RPS420 RAT spread to other devices on my network?
Yes. It supports LAN scanning, SMB exploitation, and USB propagation, allowing lateral movement across home or corporate networks.
Where can I download RPS420 RAT?
You should never download or use RPS420 RAT. It is illegal malware used for cybercrime. This article is for educational and defensive purposes only. Possession or distribution may violate cybercrime laws.
Conclusion: Don’t Let RPS420 RAT Ruin Your Digital Life
The RPS420 RAT exemplifies how far malware has come—stealthy, feature-rich, and relentlessly adaptive. But knowledge is your best weapon. By understanding its features, spotting signs early, and following our detection and removal guide, you can neutralize this threat before it escalates.
Stay vigilant in 2025’s cyber landscape. If you’ve encountered RPS420 RAT or have tips, drop a comment below. For more cybersecurity insights, check our guides on top RATs to watch or best antivirus for Windows. Secure your system today—your future self will thank you.