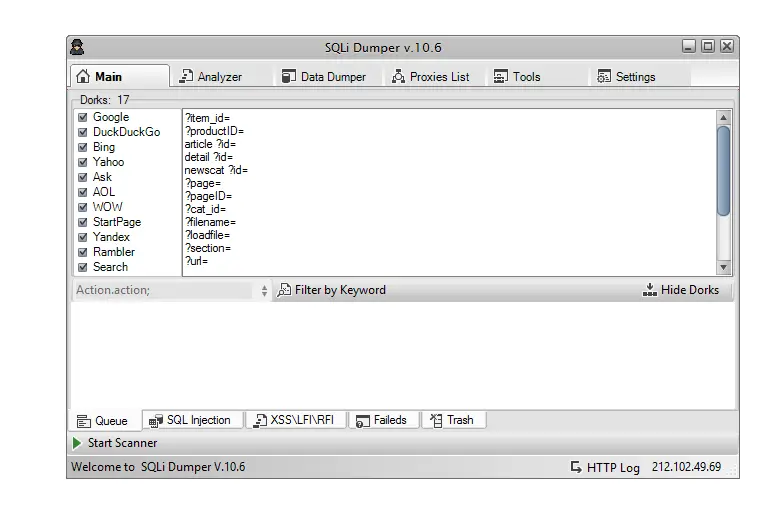
SQLi Dumper V 10.6
In the world of cybersecurity and penetration testing, tools like SQLi Dumper V 10.6 play a crucial role in identifying and exploiting SQL injection vulnerabilities. As one of the most advanced automated SQL injection exploitation tools available, SQLi Dumper V 10.6 empowers ethical hackers, security researchers, and penetration testers to simulate real-world attacks on web applications. This comprehensive guide dives deep into the features, usage, and best practices for SQLi Dumper V 10.6, helping you understand how this powerful software can enhance your security assessments—while emphasizing ethical and legal use only.
Whether you’re a seasoned cybersecurity professional or just starting with SQL injection testing, this article will cover everything you need to know about SQLi Dumper V 10.6. We’ll explore its capabilities, setup requirements, step-by-step tutorials, and more, all optimized for those searching for reliable insights into this tool.
What is SQLi Dumper?
SQLi Dumper V 10.6 is a sophisticated, open-source-inspired tool designed specifically for automating the detection and exploitation of SQL injection (SQLi) flaws in web applications. Originally developed for educational and research purposes, it has evolved into a staple for vulnerability assessment in controlled environments. Unlike manual SQL injection techniques, which can be time-consuming and error-prone, SQLi Dumper V 10.6 streamlines the process by automating database enumeration, data dumping, and exploitation workflows.
At its core, SQLi Dumper V 10.6 targets common web vulnerabilities where user inputs are not properly sanitized, allowing attackers to inject malicious SQL code. This version introduces enhanced performance optimizations and broader database compatibility compared to earlier iterations like V 8.0 or V 10.2. It’s particularly valued in bug bounty programs and red team exercises, where identifying sensitive data leaks is paramount.
Key to its appeal is its user-friendly interface, which abstracts complex SQL queries into simple point-and-click operations. However, remember: SQLi Dumper V 10.6 should only be used on systems you own or have explicit permission to test. Unauthorized use can lead to severe legal consequences under laws like the Computer Fraud and Abuse Act (CFAA).
Key Features of SQLi Dumper
What sets SQLi Dumper V 10.6 apart from generic SQL injection scanners? Its robust feature set makes it a go-to for advanced users. Here’s a breakdown of the standout capabilities:
Multithreading for Efficient Dumping
One of the biggest upgrades in SQLi Dumper V 10.6 is its support for multithreading across multiple stages of the exploitation process. This includes:
- Database enumeration: Quickly scan and identify available databases.
- Table and column dumping: Parallel processing to extract schema details faster.
- Data fetching: Retrieve records in bulk without bottlenecks.
With up to 100 threads in the exploiter module, SQLi Dumper V 10.6 can handle large-scale dumps efficiently, reducing scan times from hours to minutes on vulnerable targets.
Broad Database Support
SQLi Dumper V 10.6 isn’t limited to one backend—it’s versatile:
- MySQL
- Microsoft SQL Server (MS SQL)
- Oracle
- Sybase
- PostgreSQL
This compatibility ensures it works across diverse environments, from enterprise systems to custom web apps.
Multilingual Interface
Accessibility is key in global security teams. SQLi Dumper V 10.6 is fully translated into:
- English
- German
- Persian
- Portuguese
- Russian
- French
This makes it easier for international pentesters to collaborate without language barriers.
Built-in Analyzer and Proxy Support
The integrated analyzer in SQLi Dumper V 10.6 helps validate injection points and filter false positives. Plus, proxy integration allows for anonymized testing, crucial for evading basic detection mechanisms.
Other notable features include customizable payloads, error-based and blind SQLi modes, and export options for CSV or SQL files—perfect for reporting in tools like Burp Suite or OWASP ZAP.
System Requirements for SQLi Dumper V 10.6
Before diving in, ensure your setup meets the prerequisites for smooth operation:
- Operating System: Windows 7 or later (best on Windows 10/11).
- .NET Framework: Version 4.6 or higher.
- Visual C++ Redistributable: 2015 x86 edition.
- Hardware: At least 4GB RAM and a multi-core CPU for optimal multithreading.
Note: Always download from trusted sources and scan files with VirusTotal, as cracked or unofficial versions of SQLi Dumper V 10.6 may contain malware. Run it in a virtual machine (e.g., VirtualBox) or sandbox (e.g., Sandboxie) to isolate risks.
How to Use SQLi Dumper V 10.6: Step-by-Step Tutorial
Using SQLi Dumper V 10.6 is straightforward, but always prioritize ethics—obtain written authorization before testing any live site. Here’s a beginner-friendly guide:
Step 1: Installation and Setup
- Download the SQLi Dumper V 10.6 executable (ensure it’s a legitimate build).
- Install prerequisites via Microsoft’s official downloads.
- Launch the tool and select your preferred language from the settings menu.
Step 2: Target Identification
- Enter the vulnerable URL (e.g., http://example.com/page.php?id=1).
- Input potential injection parameters like id.
- Configure threads (start with 10-20 for testing) and proxy settings if needed.
Step 3: Vulnerability Scanning
- Hit “Start Analyzer” to detect injection types (union-based, error-based, etc.).
- Review results: SQLi Dumper V 10.6 will flag confirmed vectors with confidence scores.
Step 4: Database Enumeration and Dumping
- Once a vuln is confirmed, proceed to “Dumper” mode.
- Enumerate databases, then tables and columns.
- Select data to dump—SQLi Dumper V 10.6‘s multithreading shines here, pulling hashes, emails, or credentials rapidly.
- Export results to a file for analysis.
Step 5: Advanced Exploitation
- Use the “Exploiter” for deeper attacks, like password cracking integrations.
- Monitor progress via the real-time dashboard.
Pro Tip: Combine SQLi Dumper V 10.6 with tools like sqlmap for hybrid workflows. For video tutorials, search YouTube for “SQLi Dumper tutorial” (adapt for V 10.6 specifics).
Pros and Cons of SQLi Dumper V 10.6
Pros
- Speed and Automation: Multithreading cuts down manual effort.
- Versatility: Supports multiple DBs and injection methods.
- User-Friendly: Intuitive GUI for non-coders.
- Free and Community-Driven: Open to modifications via GitHub forks.
Cons
- Malware Risks: Unofficial downloads often bundle trojans.
- Detection Evasion Limited: Modern WAFs (e.g., Cloudflare) may block it.
- Learning Curve for Advanced Modes: Blind SQLi requires tweaking.
- Ethical Gray Areas: Misuse can lead to data breaches.
| Aspect | Pros | Cons |
|---|---|---|
| Performance | High-speed multithreading | Resource-intensive on low-end hardware |
| Compatibility | 5+ database types | Windows-only native support |
| Ease of Use | GUI-driven interface | Potential virus in cracked versions |
| Cost | Free | Hidden risks from untrusted sources |
Legal and Ethical Considerations for SQLi Dumper V 10.6
While SQLi Dumper V 10.6 is invaluable for defensive security, it’s a double-edged sword. SQL injection remains a top OWASP risk, but exploiting it without permission is illegal. Always:
- Conduct tests in isolated labs (e.g., DVWA or Mutillidae).
- Document everything for compliance (GDPR, HIPAA).
- Report findings responsibly via bug bounty platforms like HackerOne.
In 2025, with rising cyber threats, tools like SQLi Dumper V 10.6 underscore the need for proactive defense—use them to build, not break.
Alternatives to SQLi Dumper V 10.6
If SQLi Dumper V 10.6 doesn’t fit your needs, consider:
- sqlmap: Open-source, command-line powerhouse for automated SQLi.
- Burp Suite: Commercial suite with SQLi plugins for broader pentesting.
- Havij: GUI alternative, though less updated.
- NoSQLMap: For MongoDB/Redis injections.
Each has unique strengths, but SQLi Dumper V 10.6 excels in threaded dumping for large datasets.
Conclusion: Is SQLi Dumper Right for You?
SQLi Dumper V 10.6 stands as a pinnacle in SQL injection tools, blending power, speed, and accessibility for ethical security work. From multithreaded dumps to multi-DB support, it’s a must-have for any pentester’s toolkit. However, wield it responsibly—focus on securing the web, not exploiting it.
Ready to get started? Set up a safe environment and explore SQLi Dumper today. For more cybersecurity guides, subscribe to our newsletter or check our WordPress archives. Share your experiences in the comments—what’s your favorite feature of SQLi Dumper ?
This article is for educational purposes only. Always comply with local laws and obtain permissions before testing.