BTMOB V4
BTMOB V4: Understanding the Emerging Android RAT Threat in 2026
In the ever-evolving landscape of cybersecurity, new threats continue to surface, targeting mobile users worldwide. One such menace gaining attention is BTMOB V4, the latest iteration of the BTMOB RAT (Remote Access Trojan). This sophisticated Android malware poses significant risks to personal data, financial security, and device integrity. In this article, we’ll dive into what BTMOB V4 is, how it operates, its potential impacts, and essential steps to protect yourself. Whether you’re an Android user, cybersecurity enthusiast, or IT professional, staying informed about threats like BTMOB V4 is crucial for safeguarding your digital life.
What Is BTMOB V4?
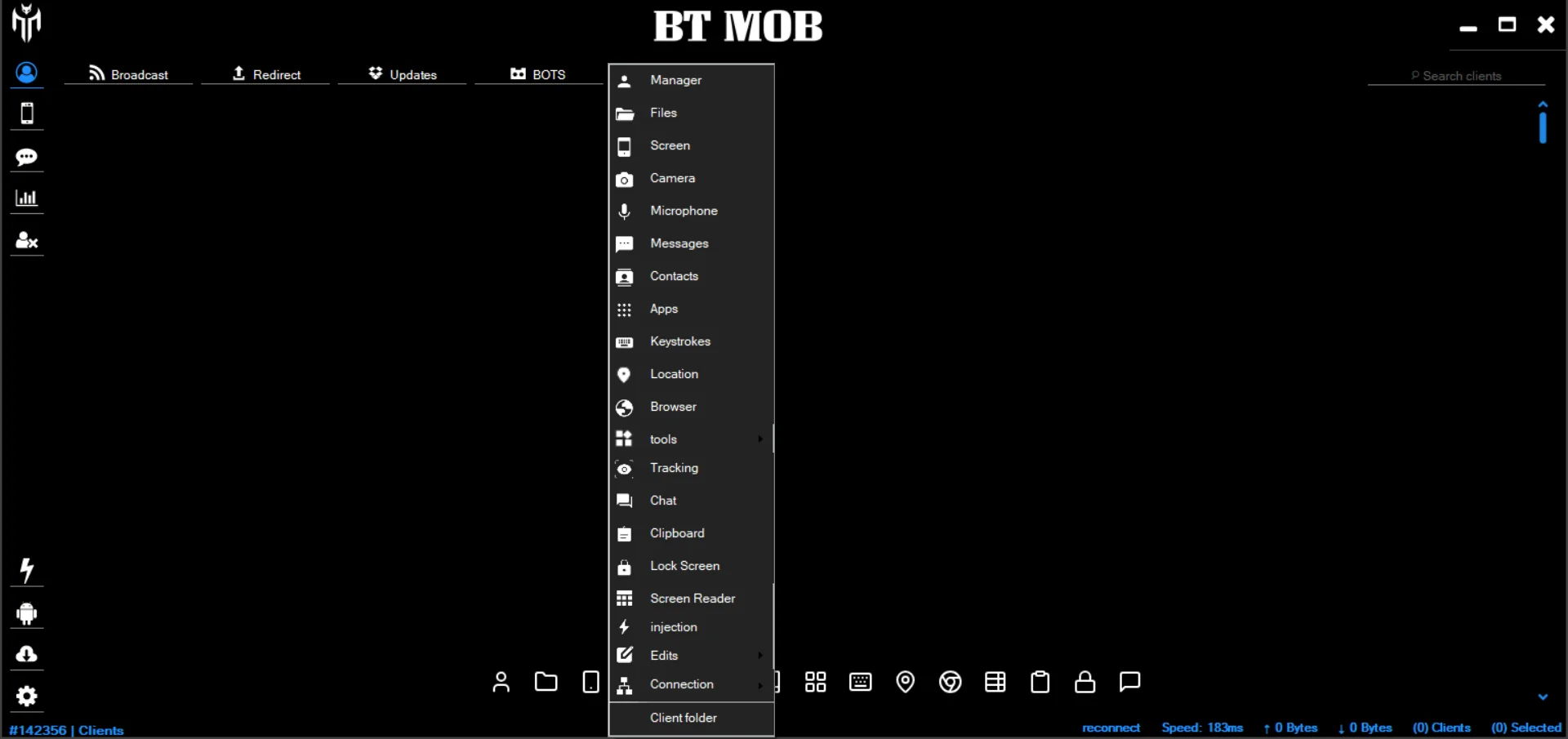
BTMOB V4 represents an advanced version of the BTMOB RAT, a malware family first identified in early 2025. According to cybersecurity researchers from firms like Cyble and Zimperium, this RAT has evolved rapidly, with versions progressing from v2.5 to v4.0 by late 2025. Marketed illicitly as a “parenting control system” or remote monitoring tool on platforms like Telegram and YouTube, BTMOB V4 is, in reality, a powerful Remote Access Trojan designed for unauthorized control of Android devices.
Key features of BTMOB V4 include:
- Remote Device Control: Attackers can manipulate screens, apps, and functions in real-time.
- Data Theft Capabilities: It steals banking credentials, passwords, clipboard data, and even Alipay PINs.
- Persistence Mechanisms: The malware survives reboots and uses obfuscation to evade detection.
- Phishing Distribution: Spread via fake apps mimicking legitimate services like streaming platforms (e.g., iNat TV), banking apps (e.g., Bradesco), or updates for popular software like Chrome or WhatsApp.

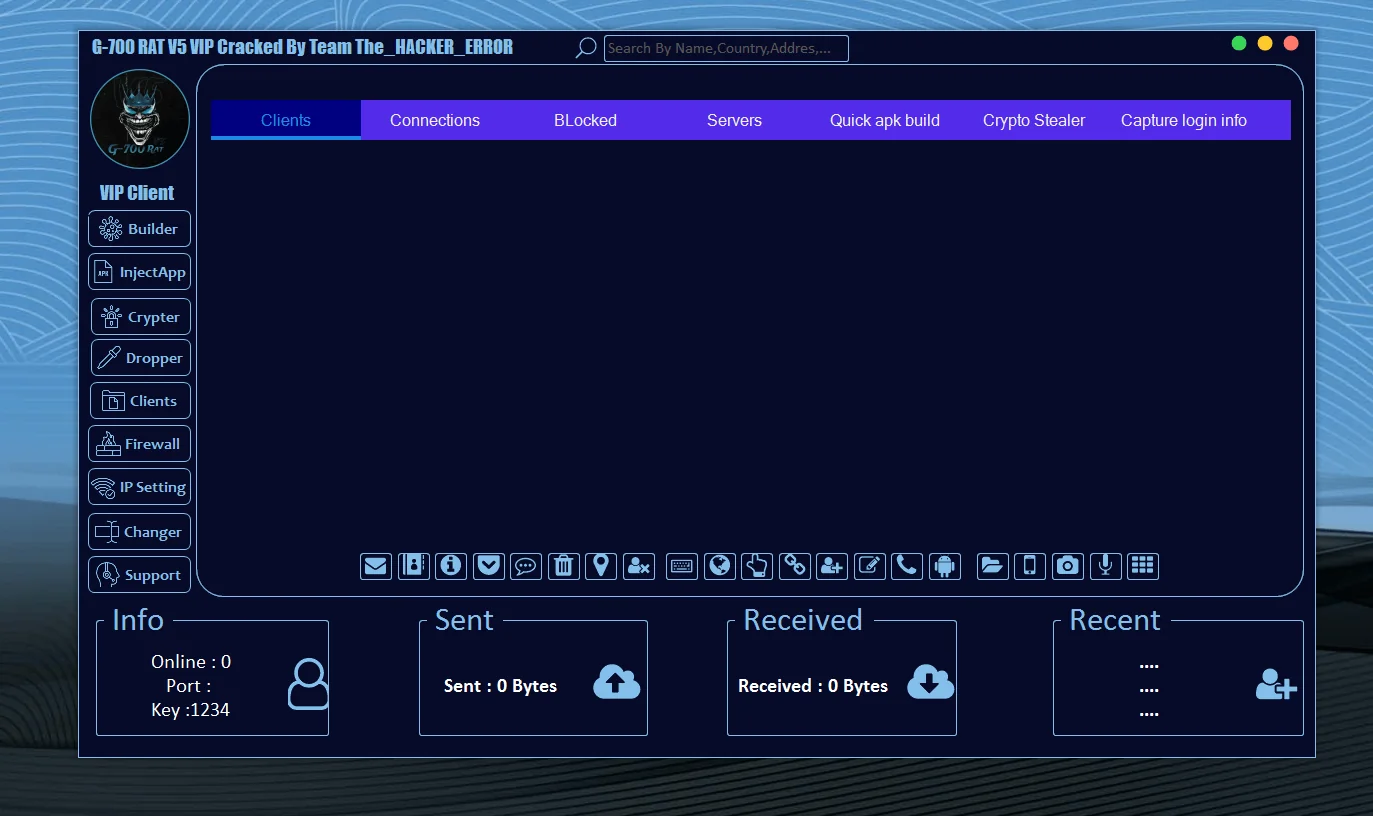
Unlike basic spyware, BTMOB V4 operates as Malware-as-a-Service (MaaS), with lifetime licenses reportedly sold for around $5,000 on underground markets. This commercial model has fueled its rapid development, making it one of the most agile Android threats in 2026.
How Does BTMOB V4 Infect Devices?
Understanding the infection vector is key to prevention. BTMOB V4 primarily spreads through phishing tactics, exploiting user trust. Here’s a breakdown of its common methods:
1. Deceptive Phishing Sites
Cybercriminals create fake websites impersonating trusted brands. Users are lured to download malicious APKs disguised as app updates or free tools. For instance, droppers posing as GB WhatsApp or Venmo have been linked to BTMOB variants.
2. Accessibility Service Abuse
Once installed, BTMOB V4 requests Android’s Accessibility Services permissions under the guise of “enhancing functionality.” This allows it to:
- Capture screen content and keystrokes.
- Simulate user interactions for unauthorized actions.
- Exfiltrate data to remote servers without alerting the user.
3. Dropper and Payload Strategy
In newer versions like v4, a “dropper” app is used to download the core payload. Victims see a fake update prompt, tricking them into installing the full RAT. This multi-stage approach helps bypass antivirus scans.
Reports from sources like ANY.RUN and Malpedia indicate over 30 droppers and 40 payloads associated with BTMOB, highlighting its widespread distribution.
The Risks and Impacts of BTMOB V4
The implications of a BTMOB V4 infection are severe, affecting individuals and organizations alike:
- Financial Losses: By targeting banking apps and wallets like Alipay, it enables credential theft leading to unauthorized transactions.
- Privacy Breaches: Full remote access means attackers can view messages, photos, and location data.
- Device Compromise: Infected devices can be used in botnets for further attacks, such as DDoS or ransomware distribution.
- Global Reach: Warnings from agencies like Morocco’s DGSSI underscore its international threat, with infections reported across Europe, Asia, and North America.
In 2025 alone, BTMOB RAT variants ranked among the top mobile threats, with thousands of samples analyzed in sandboxes like ANY.RUN.
How to Protect Yourself from BTMOB V4
Prevention is your best defense against BTMOB V4. Follow these actionable tips:
Update and Secure Your Device
- Keep Android OS and apps up to date to patch vulnerabilities.
- Enable Google Play Protect and use reputable antivirus software like those from Kaspersky or Zimperium.
Avoid Suspicious Downloads
- Only install apps from official sources like Google Play.
- Be wary of unsolicited links or “updates” from unknown sites.
Monitor Permissions
- Review app permissions carefully—question why a simple app needs Accessibility Services.
- Use tools like app vetting services to scan APKs before installation.
Enable Multi-Factor Authentication (MFA)
- Add an extra layer of security to banking and email accounts to mitigate credential theft.
If you suspect an infection, perform a factory reset and change all passwords immediately. For advanced users, tools like ADB (Android Debug Bridge) can help inspect and remove persistent threats.
BTMOB V4 in the Broader Cybersecurity Context
BTMOB V4 exemplifies the shift toward professionalized mobile malware. As Android dominates the global smartphone market (over 70% share in 2026), threats like this will likely increase. Cybersecurity experts predict more MaaS models, blending RAT capabilities with AI-driven evasion techniques.
For deeper insights, check resources from Cyble Research or Zimperium’s blog, which detail technical analyses of BTMOB variants.
Download BTMOB V4
Conclusion: Stay Vigilant Against BTMOB V4
BTMOB V4 is more than just malware—it’s a wake-up call for enhanced mobile security practices. By understanding its mechanics and adopting proactive measures, you can significantly reduce your risk. If you’re dealing with Android security in a professional setting, consider integrating threat intelligence feeds to monitor emerging RATs like this one.
Remember, cybersecurity is an ongoing process. Share this article to help others stay protected, and always verify sources before downloading anything. For the latest updates on BTMOB V4 and similar threats, bookmark reliable cybersecurity sites and enable notifications.