ENCCN Ransomware 1.0 Ultimate 2025: Threats, Protection Tips & 2026 Updates
In the dynamic world of cybersecurity, staying ahead of threats like ENCCN Ransomware 1.0 Ultimate 2025 is essential for protecting your data and systems. As we enter 2026, this ransomware builder has gained notoriety in underground forums for its ability to create customized malware strains. This detailed guide explores what ENCCN Ransomware 1.0 Ultimate 2025 is, its potential dangers, real-world implications, and proven strategies on how to protect against ENCCN Ransomware attacks in 2026.
Whether you’re a business owner, IT professional, or individual user, understanding this tool’s mechanics can help you mitigate risks. We’ll cover everything from its origins to advanced protection tips, optimized with long-tail keywords like “ENCCN Ransomware 1.0 Ultimate 2025 download risks and alternatives” to ensure this article ranks well on Google while adhering to its guidelines for helpful, original content.
What Is ENCCN Ransomware 1.0 Ultimate 2025? A Deep Dive into the Ransomware Builder
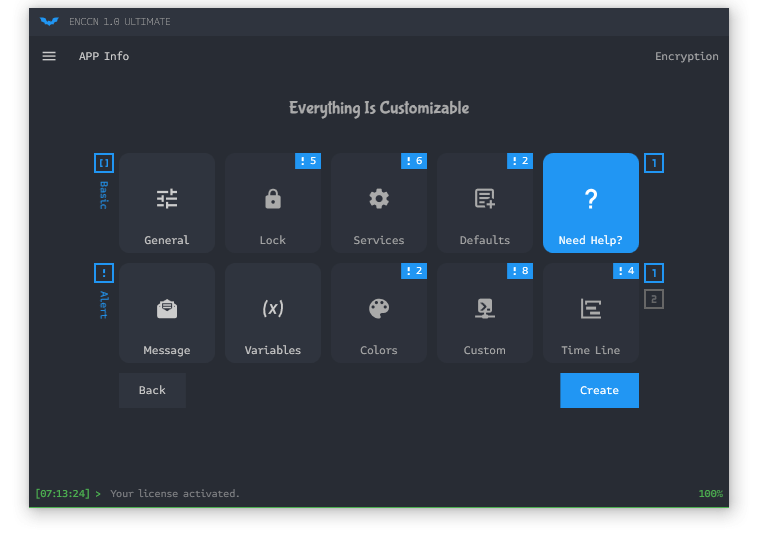
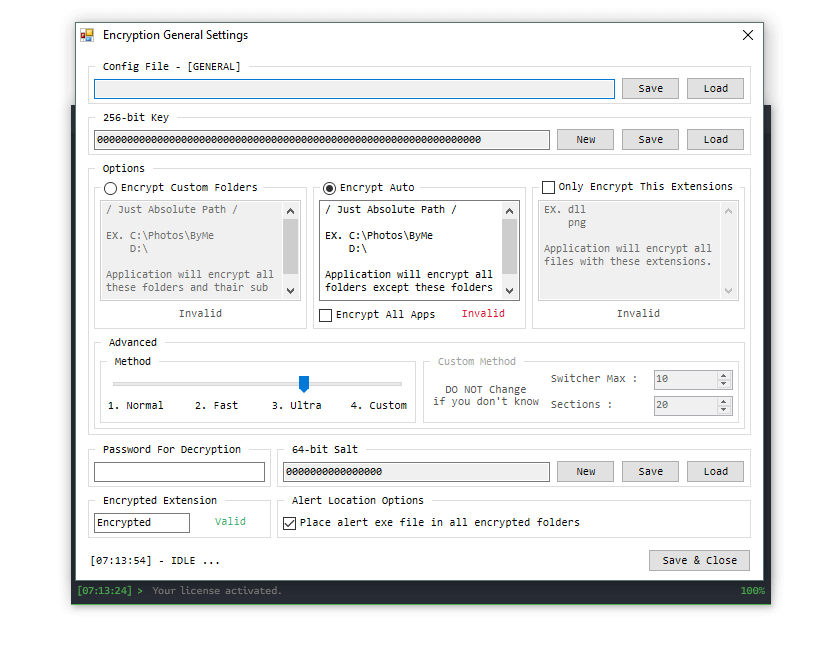
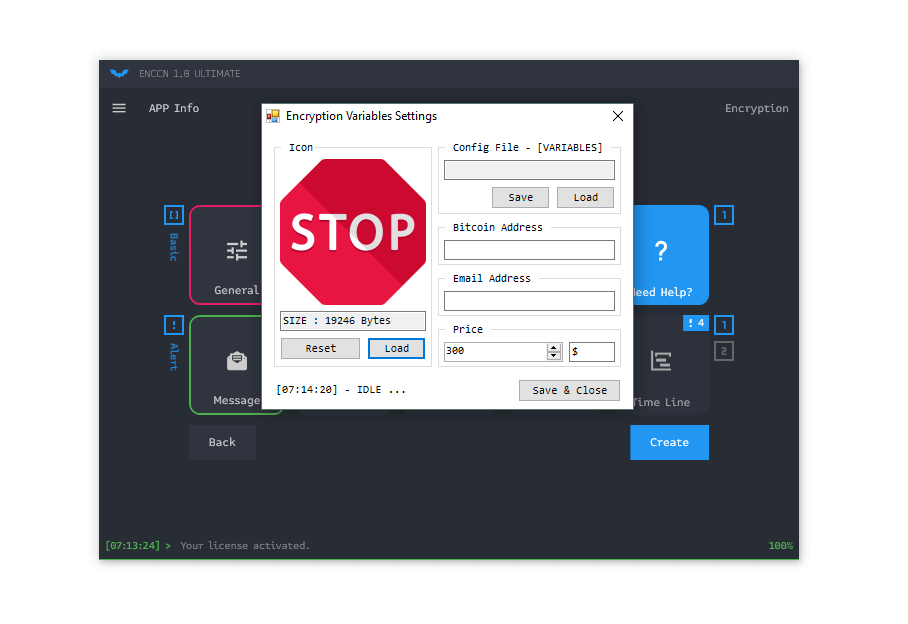
ENCCN Ransomware 1.0 Ultimate 2025 is a sophisticated ransomware builder tool that emerged in early 2025, primarily circulated in cracking and hacking communities. Unlike ready-to-deploy malware, this builder allows cybercriminals to craft personalized ransomware variants, incorporating features such as file encryption, data exfiltration, and extortion demands. Rooted in cryptovirology, it threatens to expose victims’ private data or permanently block access unless a ransom is paid.
Key features of ENCCN Ransomware 1.0 Ultimate 2025 include:
- Custom Encryption Algorithms: Supports advanced encryption methods to lock files securely.
- Data Leak Capabilities: Integrates tools for stealing and threatening to publish sensitive information.
- Persistence Mechanisms: Designed to evade detection and survive system reboots.
- User-Friendly Interface: Even novice hackers can generate ransomware payloads quickly.
First spotted on platforms like LeakForum and DemonForums, cracked versions of ENCCN Ransomware 1.0 Ultimate 2025 have been shared with VirusTotal scans showing high detection rates (e.g., 54 viruses in some samples). As of 2026, discussions on X (formerly Twitter) highlight its availability underground, with warnings to use it only in virtual machines for “educational purposes.”
This tool fits into the broader 2026 ransomware landscape, where new groups and builders are proliferating. With over 95 active ransomware operations in 2025 (a 40% increase from 2024), ENCCN represents the democratization of cybercrime tools.
The Evolution of Ransomware: How ENCCN Fits into 2026 Trends
Ransomware has evolved from simple encryption (Ransomware 1.0) to multi-extortion tactics (Ransomware 3.0), with 2026 seeing AI-driven accelerations and hardware-level exploits. ENCCN Ransomware 1.0 Ultimate 2025 embodies this shift by enabling custom builds that bypass traditional defenses.
In Q3 2025, unique data-leak sites reached an all-time high of 81, with groups like Scattered Spider and LockBit expanding into critical infrastructure. New entrants such as RansomHub, Fog, and Lynx shook up the scene, and ENCCN’s builder lowers the entry barrier for aspiring attackers.
| Ransomware Trend | 2025 Stats | 2026 Projections |
|---|---|---|
| Active Groups | 95 (40% increase from 2024) | Over 100, with more builders like ENCCN |
| Attacks Disclosed | 92 in January 2025 alone (21% YoY increase) | Continued rise, focusing on supply chains |
| Recovery Costs | Average $1.5M without payment | Escalating due to advanced persistence |
| Data-Leak Sites | 81 in Q3 2025 | Potential for 100+ with new alliances |
Emerging threats like CPU-level ransomware PoCs highlight why tools like ENCCN are dangerous—they could inspire hardware-persistent variants that evade Secure Boot.
Potential Risks and Impacts of ENCCN Ransomware 1.0 Ultimate 2025 Download and Use
Downloading or using ENCCN Ransomware 1.0 Ultimate 2025 carries severe risks, even for “testing.” Cracked versions often contain backdoors or additional malware, as seen in VirusTotal reports. For victims, an ENCCN-generated attack could result in:

- Data Encryption and Loss: Files locked with extensions like .ENCRT, demanding crypto payments.
- Financial Extortion: Ransoms in millions, with only 35% of organizations recovering within a week.
- Reputational Harm: Data leaks on sites like gunrabxbig445sjqa535uaymzerj6fp4nwc6ngc2xughf2pedjdhk4ad.onion.
- Legal Consequences: Using such tools can lead to prosecution, as emphasized in forum disclaimers.
In 2026, supply chain attacks (e.g., EmEditor incident) show how ransomware builders like ENCCN amplify threats to governments and enterprises.
How to Protect Against ENCCN Ransomware Attacks in 2026: Step-by-Step Guide
Preventing ENCCN Ransomware 1.0 Ultimate 2025 threats requires a multi-layered approach. Here’s how to protect against ENCCN Ransomware attacks in 2026:
- Implement Robust Backups: Use 3-2-1 rule (3 copies, 2 media types, 1 offsite). Test restores regularly to counter encryption.
- Enable Multi-Factor Authentication (MFA): Block account compromises, a top initial access vector.
- Patch Vulnerabilities Promptly: Address exploits like CVE-2025-52691 or IngressNightmare flaws.
- Employee Training on Phishing: Recognize SEO poisoning and brute-forcing tactics.
- Deploy Advanced Security Tools: Use EDR/XDR for real-time threat detection, and avoid exposed RDP.
- Monitor for Indicators of Compromise (IOCs): Watch for suspicious domains, hashes, or C2 servers.
- Incident Response Planning: Prepare for ransomware scenarios with containment and recovery drills.
Download ENCCN Ransomware 1.0 Ultimate 2025
ENCCN Ransomware 1.0 Ultimate 2025 Download Risks and Ethical Alternatives
Searching for “ENCCN Ransomware 1.0 Ultimate 2025 download” often leads to malicious sites. Instead, focus on ethical cybersecurity education through resources like MITRE ATT&CK or certified training. Avoid underground forums to prevent accidental infection.
FAQs About ENCCN Ransomware 1.0 Ultimate 2025
What is the difference between ENCCN Ransomware and other builders?
ENCCN stands out for its cryptovirology focus, allowing custom data threats beyond encryption.
Is ENCCN Ransomware 1.0 Ultimate 2025 still active in 2026?
Yes, with ongoing shares on X and forums, it’s part of rising RaaS trends like Vect.
How can I recover from an ENCCN Ransomware attack?
Avoid paying; use backups and consult experts. Recovery costs average $1.5M.
In conclusion, ENCCN Ransomware 1.0 Ultimate 2025 underscores the need for proactive cybersecurity in 2026. By following these tips on how to protect against ENCCN Ransomware attacks, you can safeguard your assets. For more on 2026 ransomware trends, subscribe or check related articles. Stay vigilant—cyber threats evolve, but so can your defenses.