Ultimate Stealer 1.0: An Old-School Infostealer from the Early Hacking Scene (Educational & Security Analysis Only)
In the early days of cybercrime tools (around 2009–2011), simple but effective Visual Basic programs dominated underground hacking forums. One of the most talked-about pieces of software from that era was Ultimate Stealer 1.0, created by a user known as Mr. White.
This small Windows application became infamous in Spanish-speaking hacking communities (especially on forums like Indetectables) because of its straightforward interface and dangerous functionality.
What Was Ultimate Stealer 1.0?
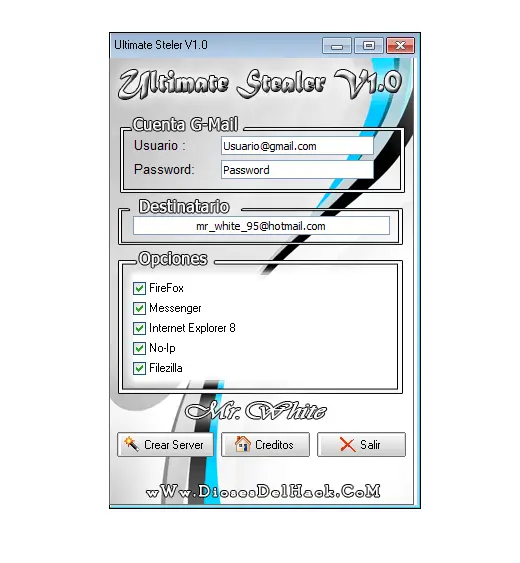
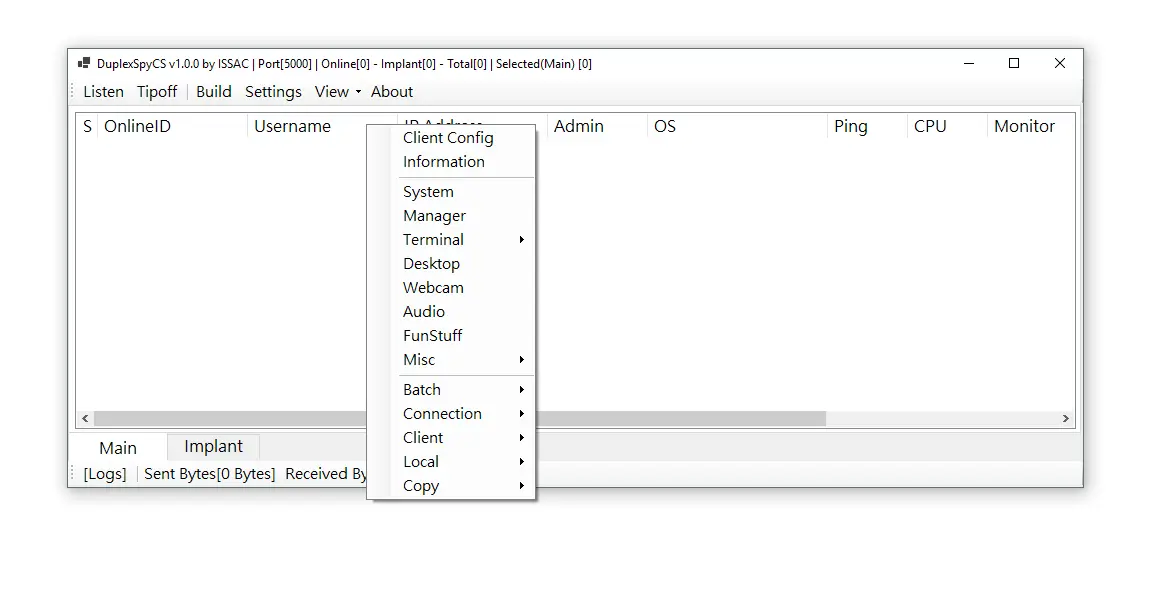
Ultimate Stealer V1.0 was a classic credential stealer (infostealer) written in Visual Basic 6. Its main purpose was to create a malicious executable (called a “stub” or “server”) that, once executed on a victim’s computer, would silently collect login credentials from popular programs and send them to the attacker’s email.
Here are the key features visible in its builder interface:
- Gmail credential harvesting section (Usuario & Password fields)
- Destination email field (where stolen logs were sent)
- Supported targets included:
- Firefox
- Messenger (likely Windows Live Messenger)
- Internet Explorer 8
- No-IP (dynamic DNS accounts)
- FileZilla (FTP client)
After configuring these options, the user clicked “Crear Server” (Create Server) to generate the malicious .exe file.
Here’s how the original builder interface looked:
How Did Ultimate Stealer 1.0 Work Technically?
The program used very primitive (by today’s standards) but effective methods:
- It collected saved passwords and auto-login data from the selected applications.
- Used Microsoft CDO (Collaboration Data Objects) to send emails directly through a Gmail account.
- The attacker only needed to provide a throwaway Gmail address and password in the builder.
- No advanced encryption, no C&C server, no web panel — just plain email delivery.
This made it extremely easy to use even for beginners, which is why it became popular in 2010 among script-kiddies.
Why Is Ultimate Stealer Considered Historical Malware in 2026?
Today (2026), the infostealer landscape has dramatically evolved:
- Modern stealers like RedLine, Vidar, Raccoon, Lumma, Stealc and even newer ones like VVS Stealer use:
- Webhook exfiltration (Discord/Telegram)
- Browser wallet draining (crypto)
- Clipboard hijacking
- Real-time session hijacking
- Heavy obfuscation (Pyarmor, etc.)
- Malware-as-a-Service business model
Ultimate Stealer 1.0 represents the stone age of stealers — simple, noisy, email-based, and easily detected even by 2010 antivirus software (most samples showed 80%+ detection rate on VirusTotal back then).
Yet it clearly shows the DNA of modern stealers: target popular software → collect credentials → exfiltrate silently.
Security Lessons from Ultimate Stealer 1.0 in 2026
Even though this malware is ancient, the techniques it used are still relevant:
- Never run unknown .exe files (especially from forums or chats)
- Use password managers instead of browser/auto-save
- Enable 2FA/MFA everywhere possible
- Keep browsers and email clients updated
- Antivirus + common sense remains the best defense
Download Ultimate Stealer 1.0
Final Thoughts
Ultimate Stealer 1.0 by Mr. White is not a tool you should ever use or try to “update” — it’s a relic of early 2010s cybercrime used only for educational and historical cybersecurity analysis.
Understanding where infostealers came from helps appreciate how far both attackers and defenders have come in the last 15+ years.