Doge Rat 2026 – Technical Analysis, Features, and Cybersecurity Research Overview
Introduction to Doge Rat 2026
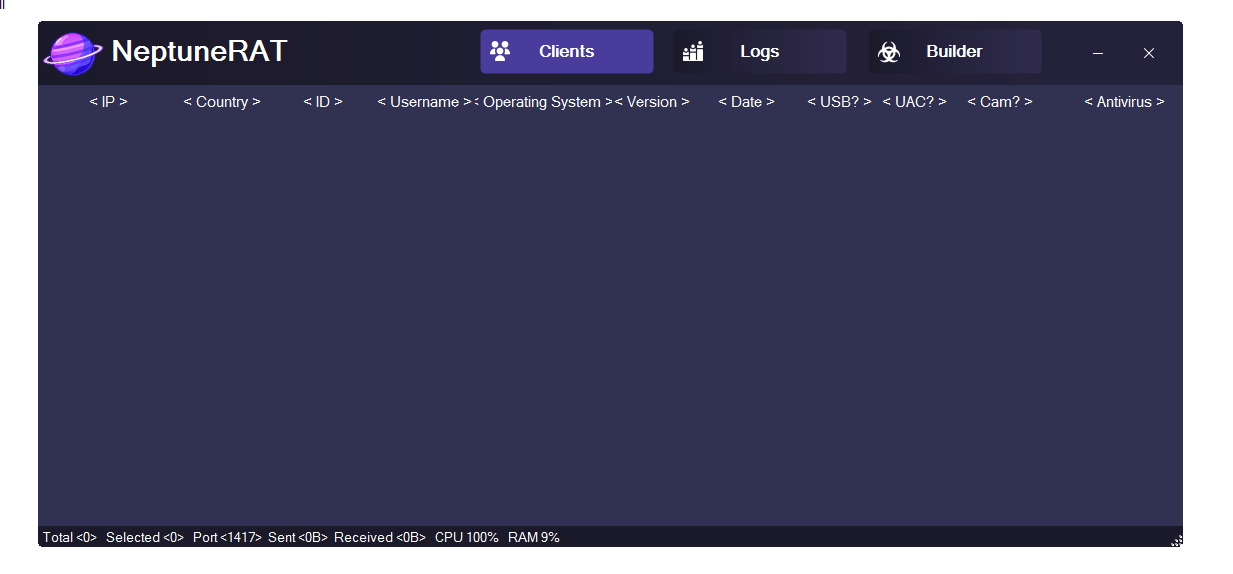
Doge Rat 2026 is an open-source Remote Access Tool (RAT) available on GitHub that is primarily analyzed within the context of cybersecurity research, malware analysis, and ethical hacking education. Tools like Doge Rat help security professionals understand how modern remote access threats operate so that better detection, prevention, and incident response strategies can be developed.
This article provides a high-level technical overview of Doge Rat 2026, its architecture, features, and cybersecurity implications, strictly for educational and defensive research purposes.
What Is Doge Rat?
Doge Rat is a command-and-control (C2) based remote access tool that allows an operator to remotely interact with a target system. Such tools are often studied by malware analysts to understand attacker techniques, persistence mechanisms, and communication models.
⚠️ This discussion is intended only for learning, malware research, and defensive security analysis.
Doge Rat 2026 Architecture Overview
Doge Rat 2026 follows a client–server model, commonly seen in RAT frameworks:
- Client Component: Executes on the target system and communicates with the server
- Server / Controller: Issues commands and receives data
- Network Communication: Enables remote execution and monitoring
- Modular Design: Allows extension and feature testing
This architecture is useful for studying real-world attack simulations in controlled lab environments.
Key Features of Doge Rat 2026
From a technical and analytical standpoint, Doge Rat 2026 demonstrates several behaviors commonly observed in modern RAT families:
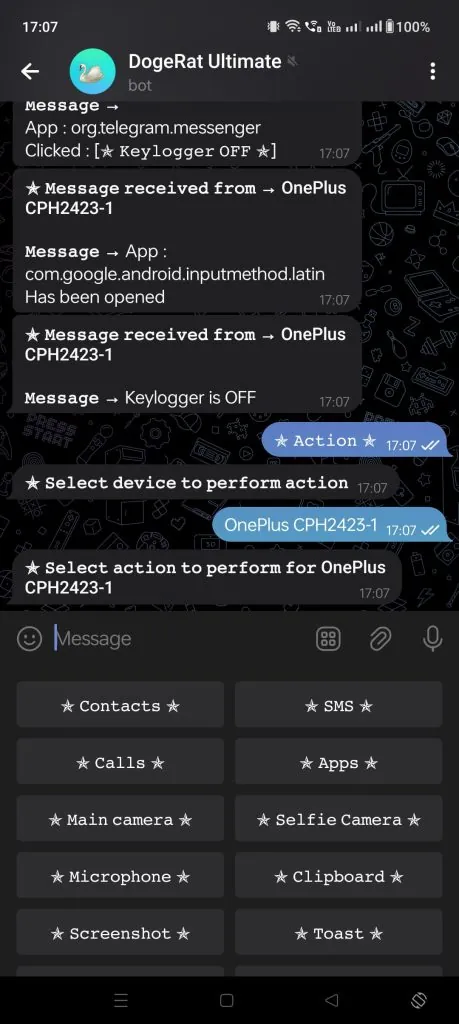
1. Remote Command Execution
Allows execution of system-level commands remotely, useful for studying privilege abuse and detection rules.
2. System Information Collection
Demonstrates how attackers gather:
- OS details
- Hardware information
- Environment variables
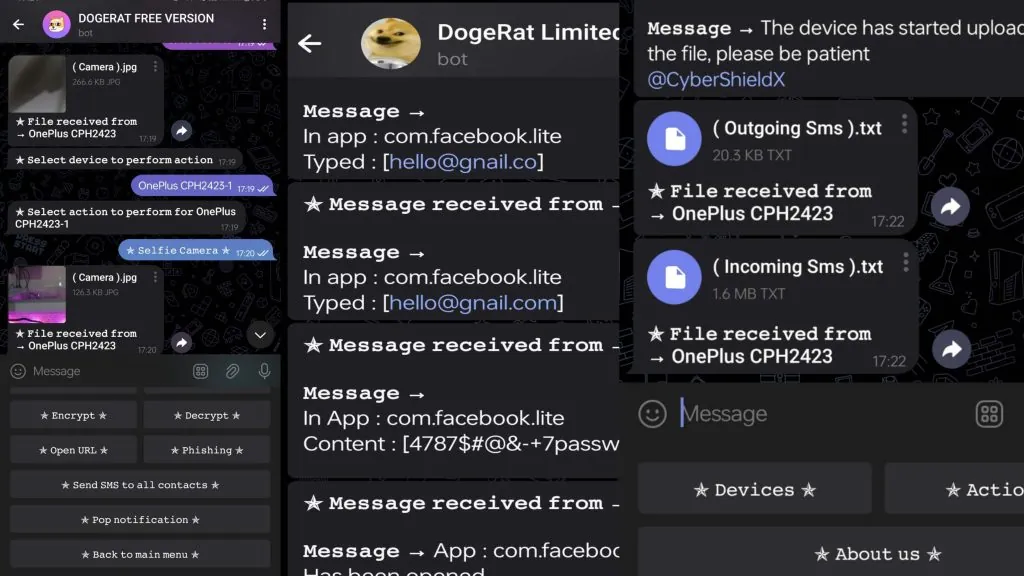
3. File Management Capabilities
Includes basic file interaction methods, helping analysts understand data exfiltration techniques.
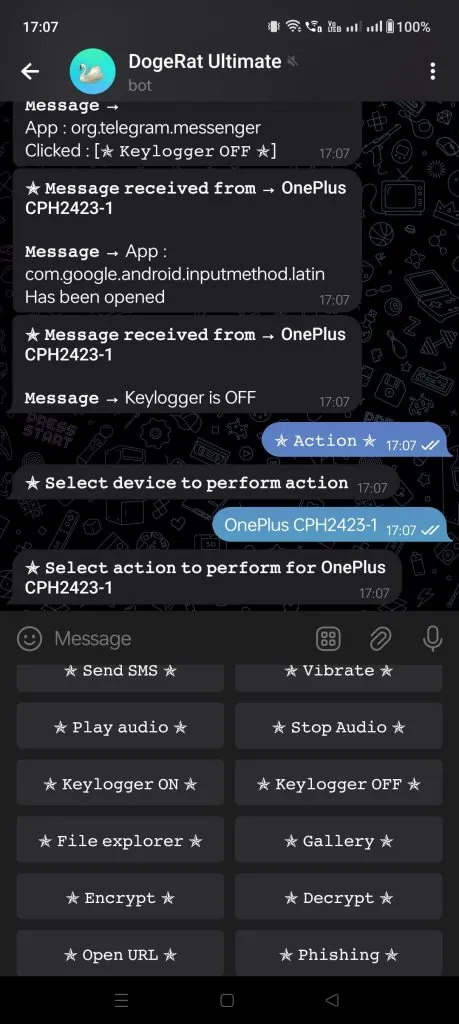
4. Persistence Techniques (Research Context)
Shows how malware attempts to survive reboots, which helps defenders build persistence detection mechanisms.
5. Network Communication Behavior
Useful for learning:
- Traffic pattern analysis
- Signature-based detection
- Anomaly-based monitoring
Educational and Research Use Cases
Doge Rat 2026 can be studied in:
- Malware analysis labs
- Blue team defensive training
- SOC detection engineering
- Academic cybersecurity research
- Ethical hacking courses
Understanding such tools strengthens endpoint security, IDS/IPS rules, and EDR solutions.
Cybersecurity Risks and Ethical Considerations
While Doge Rat 2026 is publicly accessible, unauthorized deployment or misuse is illegal and unethical. Researchers must ensure:
- Usage only in isolated lab environments
- Explicit authorization for testing
- Compliance with local cybercrime laws
Security awareness and ethical responsibility are critical in cybersecurity research.
How Security Teams Defend Against RAT Threats
Studying Doge Rat 2026 enables defenders to improve:
- Behavioral malware detection
- Network traffic monitoring
- Endpoint protection rules
- Threat intelligence correlation
- Incident response playbooks
Prevention is strongest when attackers’ tools are well understood.
Download Doge Rat 2026
Final Thoughts
Doge Rat 2026 serves as an educational example of how remote access malware operates. By analyzing such tools responsibly, cybersecurity professionals can enhance defensive strategies and reduce real-world cyber risks.
Knowledge of threats is the foundation of strong digital defense.
Disclaimer
This content is published strictly for educational, academic, and defensive cybersecurity research purposes. The author does not support or encourage illegal or unethical use of any software discussed.